Azure API Management example
Use Azure API Management as a gateway between your Azure environment and Deeploy. With Azure API Management you can enable fine grained access control, enhanced monitoring and error handling.
Create Application Registration
For this example we will create a new Application Registration called deeploy.
Optionally configure your Application Registration to use the v2 Active Directory tokens by setting "accessTokenAcceptedVersion": 2 in your App Registration manifest.
In "Expose an API" enable the Application ID URI, you need this for creating access tokens (JWTs) for this Application Registration.
Create API Management Service API
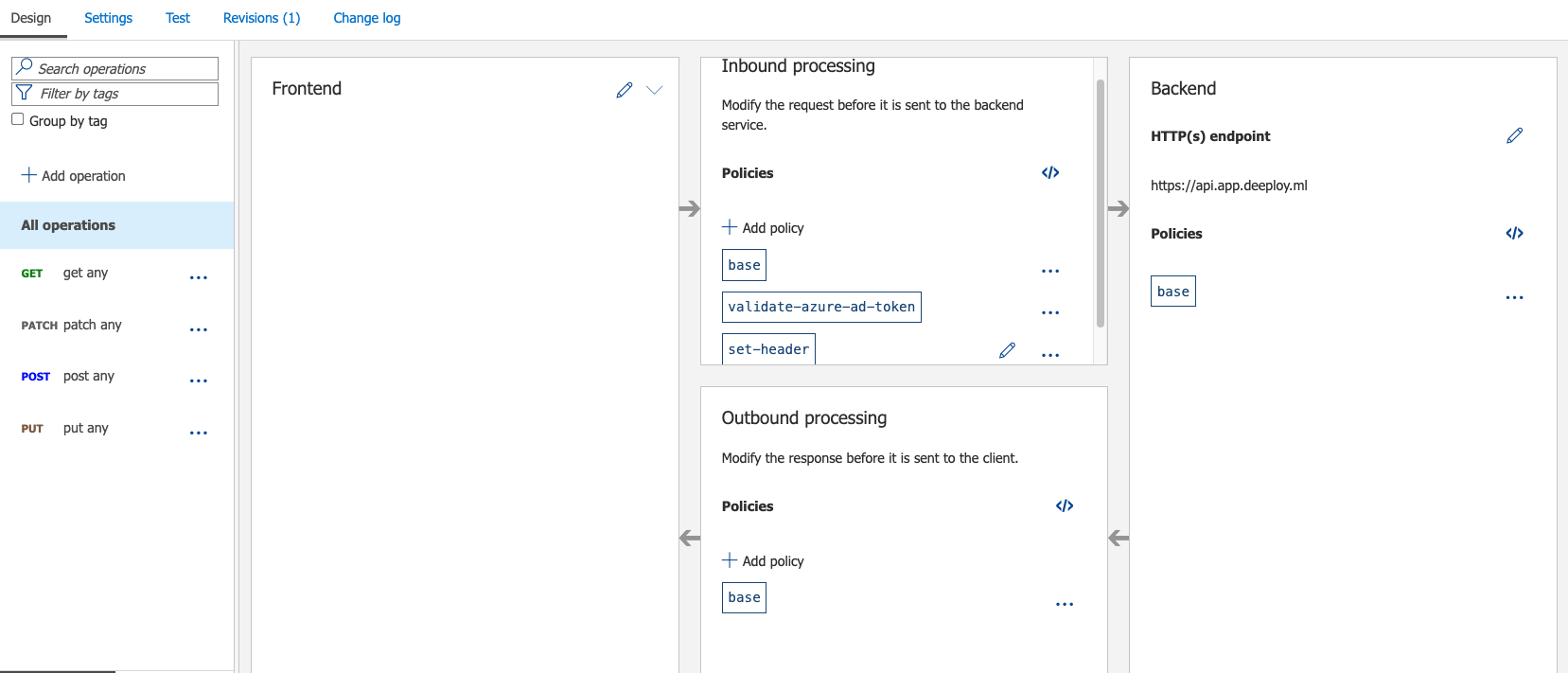
In your API Management Service, go to the API section under the API tab. Create a new HTTP api, pointing to your Deeploy API URL. For Deeploy Cloud use https://api.app.deeploy.ml.
In your newly created API, expose the endpoints you would like to connect to. For this example we expose all GET, PATCH, PUT and POST endpoints by using wildcards (*) as URL.
For Deeploy Cloud add the set-header inbound processing policy on your operations. As key use team-id and as value use your Deeploy Team ID. Your API should look similar to:
Integrate Azure AD provider in Deeploy
See Configure OpenID Connect to let Deeploy allow tokens issued by your Azure AD provider. As audience, use the Object ID of the Enterprise Application corresponding to your Application Registration (is created automatically).
For testing purposes we will obtain an access token for the Application Registration with the Azure CLI. The token has the Application Registration Application ID as subject, so make sure to add that on your Deployment's authentication page.
To obtain a token, execute:
az account get-access-token --scope api://<Application Registration Application ID>/.default.
With this token you can interact with your Deployment, using your API Management Service URL.
To make a prediction using bash:
curl -X POST "https://<API Name>.azure-api.net/workspaces/<Workspace ID>/deployments/<Deployment ID>/predict" \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer <JWT>' \
-d '{
"instances": [
[39, 7, 1, 1, 1, 1, 2174, 0, 40, 9],
[44, 12, 1, 1, 1, 1, 10000, 0, 30, 2]
]
}'